In the previous article , I mentioned that I set up a BT offline download server based on Aria2. To deploy the container with Caddy as a reverse proxy, I uninstalled the Trojan that I had lazily deployed using a one-click script before. The reason is simple: the script occupied ports 80 and 443, making it impossible to continue without uninstalling it.
So, the offline download server was set up, but the proxy that was occasionally needed had to be taken offline. After some thought, I recalled seeing someone revive a blocked VPS using Cloudflare + V2Ray + WS. Since it’s WebSocket, it can be reverse proxied by Cloudflare, so why not use Caddy? Moreover, Caddy has automatic TLS, which is certainly easier to configure than the Nginx + Certbot combination. Once configured successfully, I can run the proxy while keeping port 443 for Caddy.
Installing VLESS and Caddy
You can install VLESS directly using the v2fly/fhs-install-v2ray one-click script:
| |
For installing Caddy, please refer to the official tutorial . For example, if I use Debian 12, I would use the following commands:
| |
Configuring VLESS
Edit /usr/local/etc/v2ray/config.json:
| |
Save and exit after editing.
Configuring Caddy
Create a Caddyfile in your preferred location, or edit an existing Caddyfile, adding the following content to reverse proxy the port set in the VLESS configuration file:
| |
At this point, all the editing work for server configuration files are done.
Starting the Services
Start VLESS and set it to start on boot:
| |
Start Caddy or update the Caddy configuration:
| |
After completing all the above steps, the Caddy reverse proxy for VLESS is done.
Client Configuration
Client settings need to be done manually:
- The address should be the domain bound to VLESS.
- The port should be 443.
- TLS should be enabled.
- The transport method should be WebSocket.
- The UUID should be the one defined in the VLESS configuration file.
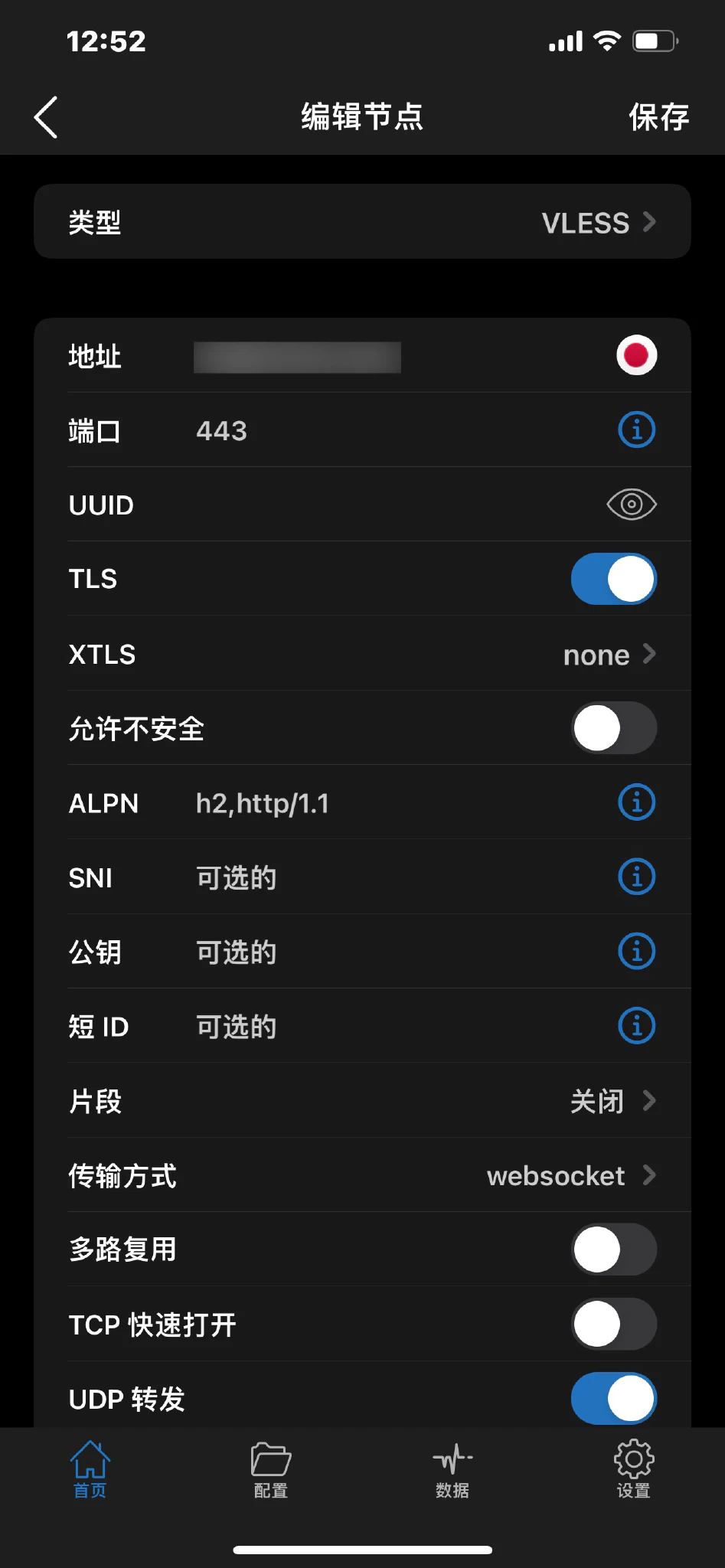
Most client settings are similar. For Clash configuration files, you can refer to the Mihomo documentation 1. Below is my example configuration file:
| |
To generate a Clash configuration file, you can use the tool provided by V2RaySE .
Conclusion
Now we have a VLESS server, and Caddy will automatically apply for and maintain the TLS certificates for us, which is very convenient.
With just a little effort, I feel the same joy as when I used one-click scripts to set up SSR back in the day. Enjoy the excitement of being able to smoothly open google.com.
TODO List
- Basic setup
- Camouflage
After all, Mihomo, inheriting the Clash Meta mantle, is considered the true successor of Clash. ↩︎

Comments are disabled until you accept functional cookies.