When using the internet in China, there are two common DNS-related issues: DNS poisoning and DNS leaks. To ensure a smooth browsing experience, these problems must be addressed.
What is a DNS Leak?
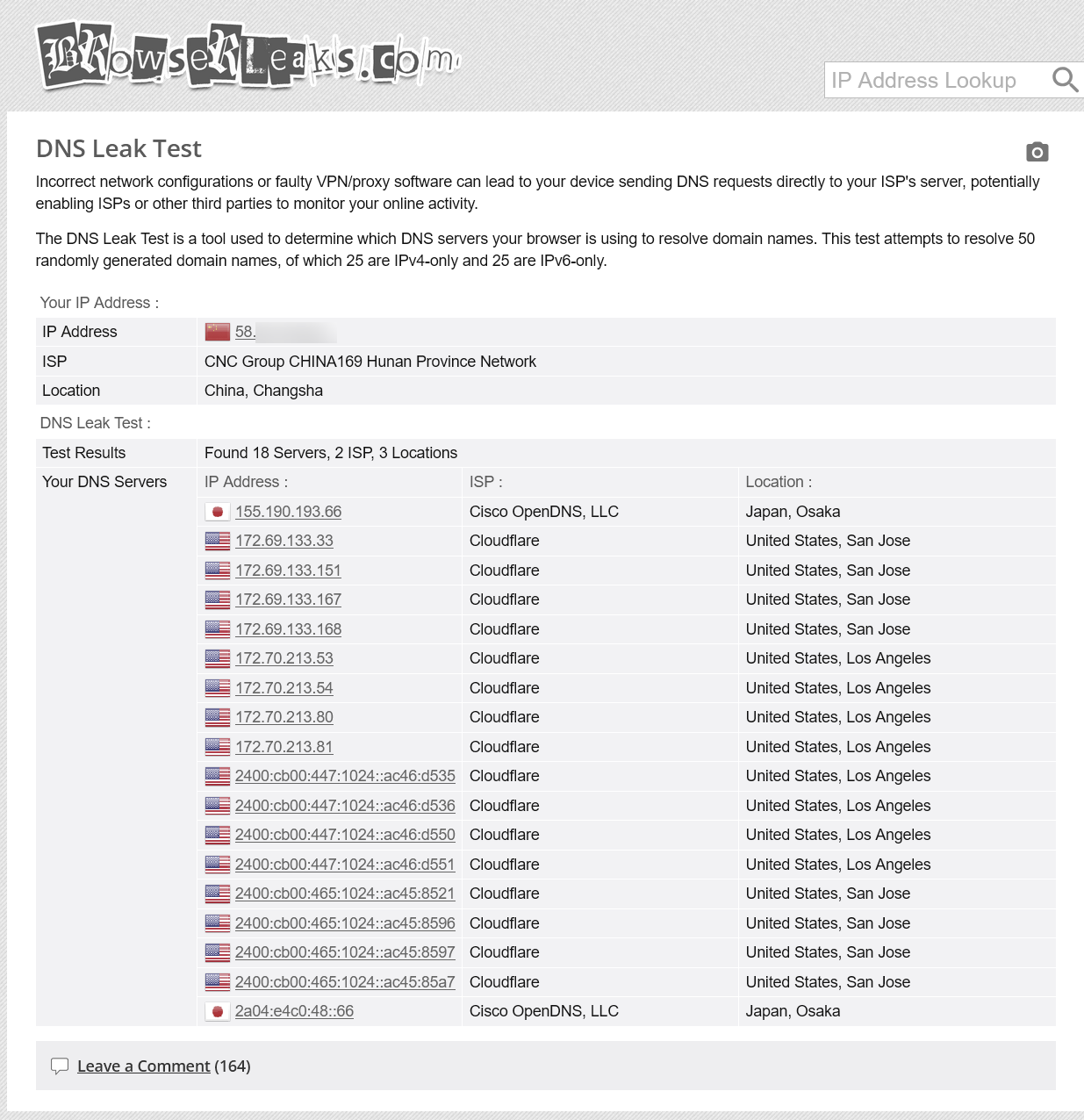
If you’re currently using a proxy to read this article, you can first visit this website to check whether your DNS requests are being sent to domestic DNS servers.
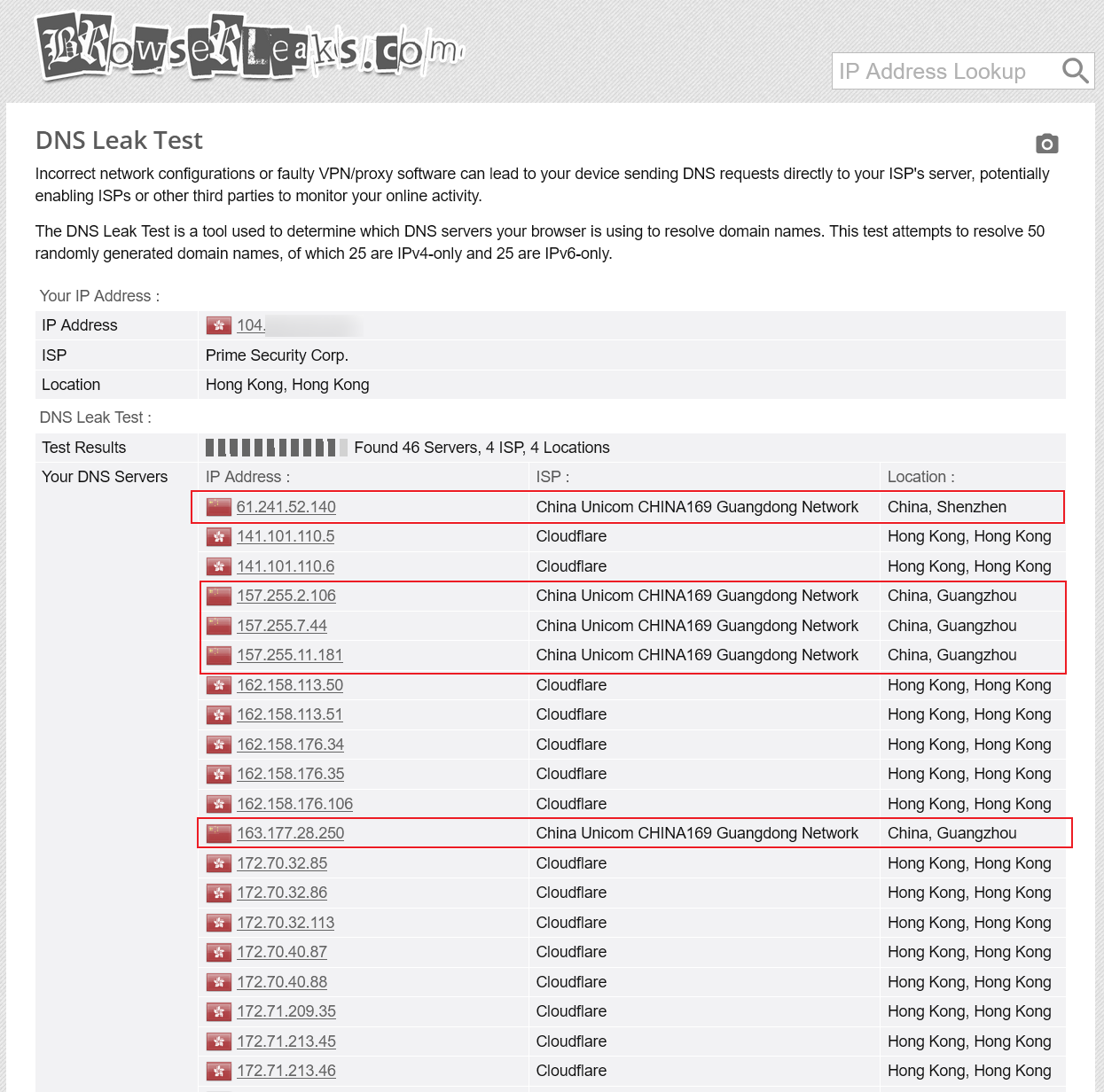
In simple terms, when you use a VPN or other proxy tools, you might think that your requests are only visible to you and your VPN provider. However, your device’s DNS requests could still be sent to your ISP’s DNS servers or public DNS servers (such as those provided by Alibaba or Tencent) for resolution. This means your real IP address and the domain names you visit could be logged. If you’re resolving sensitive domain names (like Telegram or WikiLeaks), this could attract regulatory attention, potentially resulting in warnings or even being summoned for questioning. 1
Therefore, it’s crucial to configure your proxy tool’s routing strategies properly to avoid DNS leaks.
Configuring SmartDNS
Preventing DNS Leaks
DNS acts as the guide for your internet connection, so it must be fast. Deploying SmartDNS locally as your home network’s DNS server is an excellent choice. For details on SmartDNS’s functionality, configuration tips, and how it optimises CDN selection to speed up browsing, Sukka’s article “I Have My Unique DNS Setup” is highly recommended. Before proceeding with this article, it’s worth reading Sukka’s guide, as it covers many foundational aspects that won’t be repeated here. This article will focus on implementing these configurations via the Luci interface.
If, like me, you’re using OpenWRT, note that SmartDNS’s Luci app automatically generates new configuration files based on the settings saved in its interface each time it starts up. Therefore, refrain from directly modifying the configuration files in the /etc/smartdns directory. All changes should be made through the Luci app.
Generally, the more upstream servers SmartDNS has, the better. A higher number of upstream servers does not impact SmartDNS’s performance2, and it also increases redundancy. To prevent DNS leaks, ensure that foreign upstream DNS servers (preferably encrypted ones) are added to the default group, while domestic servers are placed in a separate group (e.g., domestic) with the additional parameter -exclude-default-group to exclude them from the default group.
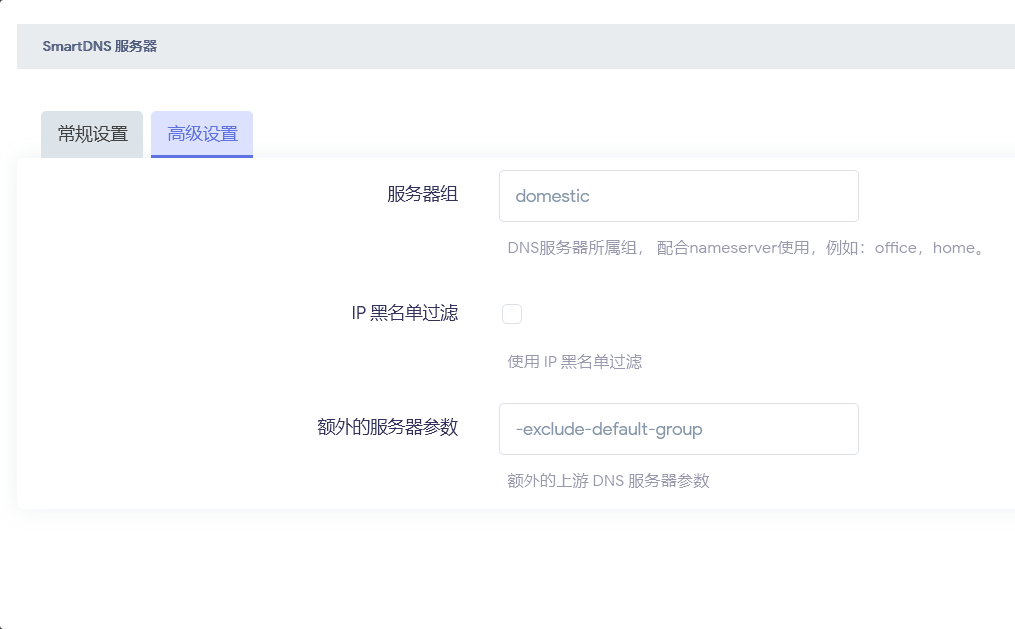
Accelerating Domestic Domain Resolution
Once foreign upstream servers are configured, DNS leaks are no longer an issue. However, excluding domestic upstream servers from the default group means that accessing new domains requires waiting for responses from foreign upstream servers, which can slow down access to domestic websites and degrade CDN performance.
The dnsmasq-china-list project by Felix Yan provides a solution. It supports generating SmartDNS-compatible configuration files via Makefile. Some contributors have even automated daily updates via GitHub Actions, so you can directly download ready-made files. Note that these configuration files only work if the domestic upstream server group is named domestic.
| |
Next, import these configuration files into SmartDNS by pasting the following into the “Custom Settings” section.
| |
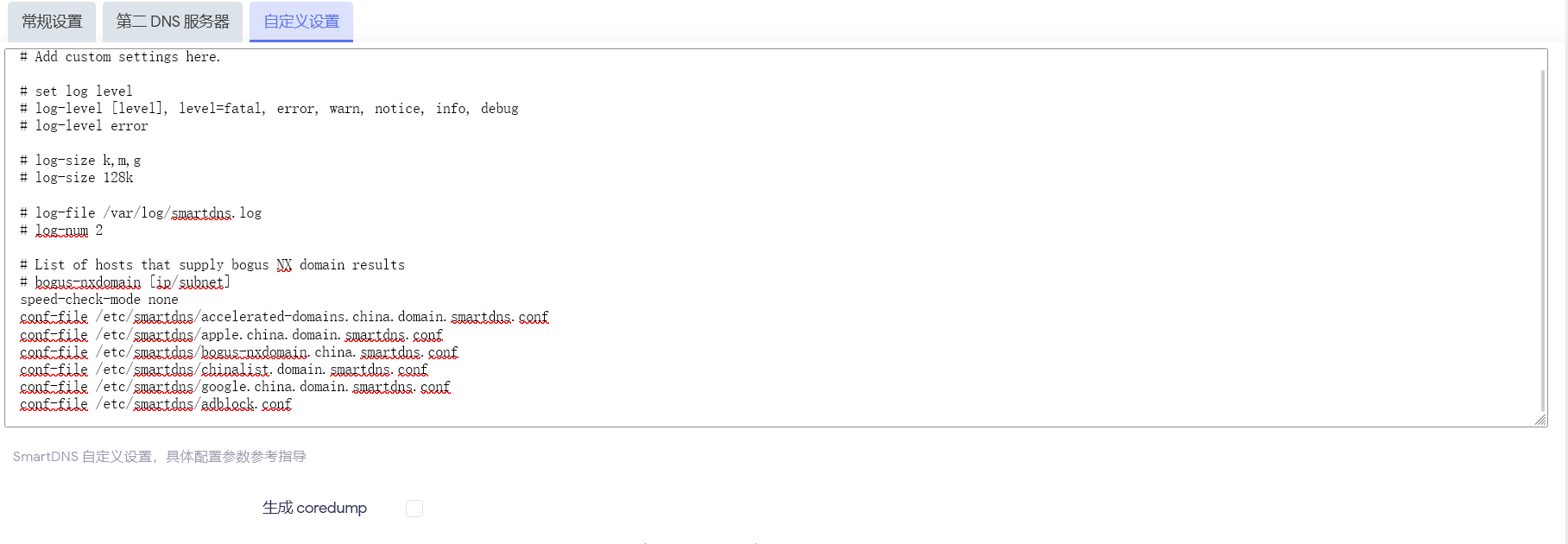
With this setup, domestic domain resolution will no longer be slowed down, and DNS leaks won’t occur when accessing foreign domains.
Ad Blocking
While DNS-level ad blocking has its limitations, the focus should be on avoiding false positives. Avoid using the infamous3 Anti AD list, which claims to be the “most accurate ad-blocking list in the Chinese-speaking community.” Instead, opt for alternative rules. I personally use 217heidai/adblockfilters, a well-curated aggregated rule set that can be pulled directly.
| |
Finally, import the configuration file:
| |
Automating Rule Updates
Set up the following Crontab to automatically update all rules daily at 3 a.m.
| |
Can a Secondary Router Be Used?
Unless IPv6 is completely disabled, it’s best to use the OpenWRT router as the primary router. When used as a secondary router, certain systems (looking at you, Windows) may ignore the IPv4 DNS broadcast by the secondary router and insist on using the IPv6 DNS broadcast by the ISP’s modem. I’ve tried modifying related registry keys, but to no avail. Ultimately, I had to call my ISP to switch the modem to bridge mode and use OpenWRT as the primary router.
Overriding Clash Rules
Even after configuring SmartDNS, running a DNS leak test while using Clash will likely show DNS requests being sent to Chinese DNS servers. This is because most VPN providers’ default configurations use encrypted DNS services from domestic tech giants like Tencent or Alibaba. While this prevents plaintext leaks to ISP DNS servers (and thus avoids calls from anti-fraud centres), it can still be unsettling for privacy-conscious users. Some providers don’t even include relevant configurations.
Fortunately, if you’re using Clash Verge Rev, it’s easy to override the provider’s configuration. Below is my override configuration, which can be pasted into the global extension configuration to replace the provider’s settings.
| |
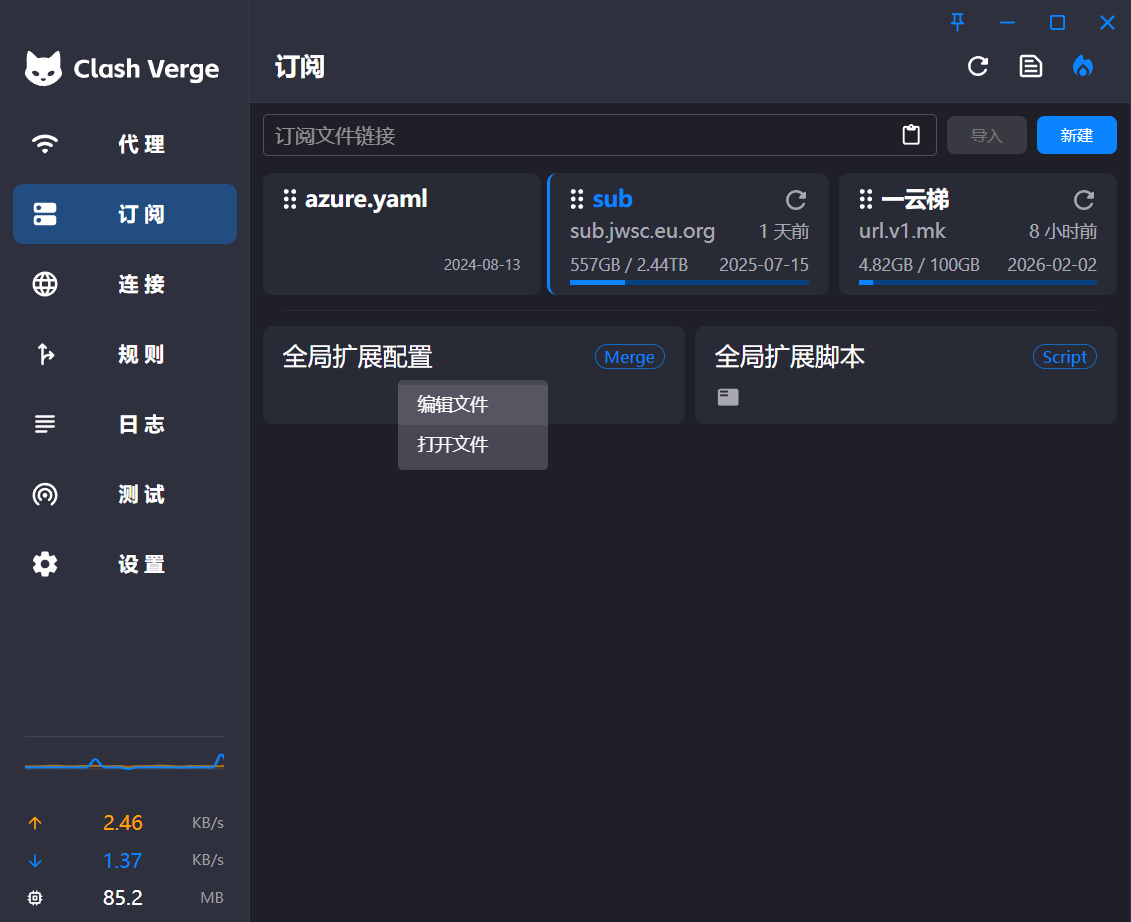
Configuration Analysis
According to Mihomo’s documentation4, the DNS request flow is as follows:
flowchart TD Start[Client initiates request] --> rule[Matches rules] rule --> Domain[Matches domain-based rules] rule --> IP[Matches IP-based rules] Domain --> |Matched direct connection rule|DNS IP --> DNS[Resolves domain via Clash DNS] Domain --> |Matched proxy rule|Remote[Resolves domain via proxy server and establishes connection] Cache --> |Redir-host/FakeIP-Direct miss|NS[Matches nameserver-policy and queries] Cache --> |Cache hit|Get Cache --> |FakeIP miss, proxy domain|Remote NS --> |Match successful| Get[Uses resolved IP to match IP rules] NS --> |No match| NF[nameserver/fallback concurrent queries] NF --> Get[Query resolved IP] Get --> |Cache DNS result|Cache[(Cache)] Get --> S[Direct/proxy connection via IP] DNS --> Redir-host/FakeIP Redir-host/FakeIP --> |Query DNS cache|Cache
The nameserver-policy has a higher priority than nameserver and fallback. By specifying that websites in geosite:cn are resolved via the system DNS (i.e., SmartDNS), you can enjoy LAN-level response speeds and built-in CDN optimisation. Websites not in geosite:cn are resolved via nameserver/fallback, ensuring the reliability of results and preventing DNS leaks by using encrypted foreign upstream servers.
Replacing GeoIP and GeoSite Databases
Mihomo uses the official V2Ray GeoIP and GeoSite databases by default. However, these databases are somewhat incomplete and updated infrequently. I recommend replacing them with the enhanced Loyalsoldier/v2ray-rules-dat database. Simply download geoip.dat and geosite.dat and place them in the kernel directory. Alternatively, add the following override configuration for automatic/one-click updates:
| |
Clash Meta for Android
For Clash Meta for Android (referred to as Clash), override settings should take into account the specific needs of mobile devices.
The Clash mobile app offers fewer flexible override options than the desktop version, Clash Verge Rev. Additionally, mobile devices frequently switch network environments, causing system DNS to change frequently. In such cases, testing shows that Clash needs to be toggled off and on again after each network change to refresh the system DNS. As a workaround, you can use a fixed domestic encrypted DNS for domestic queries.
Navigate to Clash -> “Settings” -> “Override” and configure the following:
- “DNS” -> “Policy”: Force enabled
- “DNS” -> “Prefer h3”: Enabled
- “DNS” -> “Name Server”: Add two foreign encrypted DNS servers
- “DNS” -> “Name Server Policy”: Enter
geosite:cnin the “Key” field andhttps://doh.pub/dns-queryin the “Value” field.
Download geoip.dat and geosite.dat from GitHub in advance, then go to Clash -> “Settings” -> “Meta Features” and use the “Import GeoIP Database” and “Import GeoSite Database” options to import them.
Wrapping Up
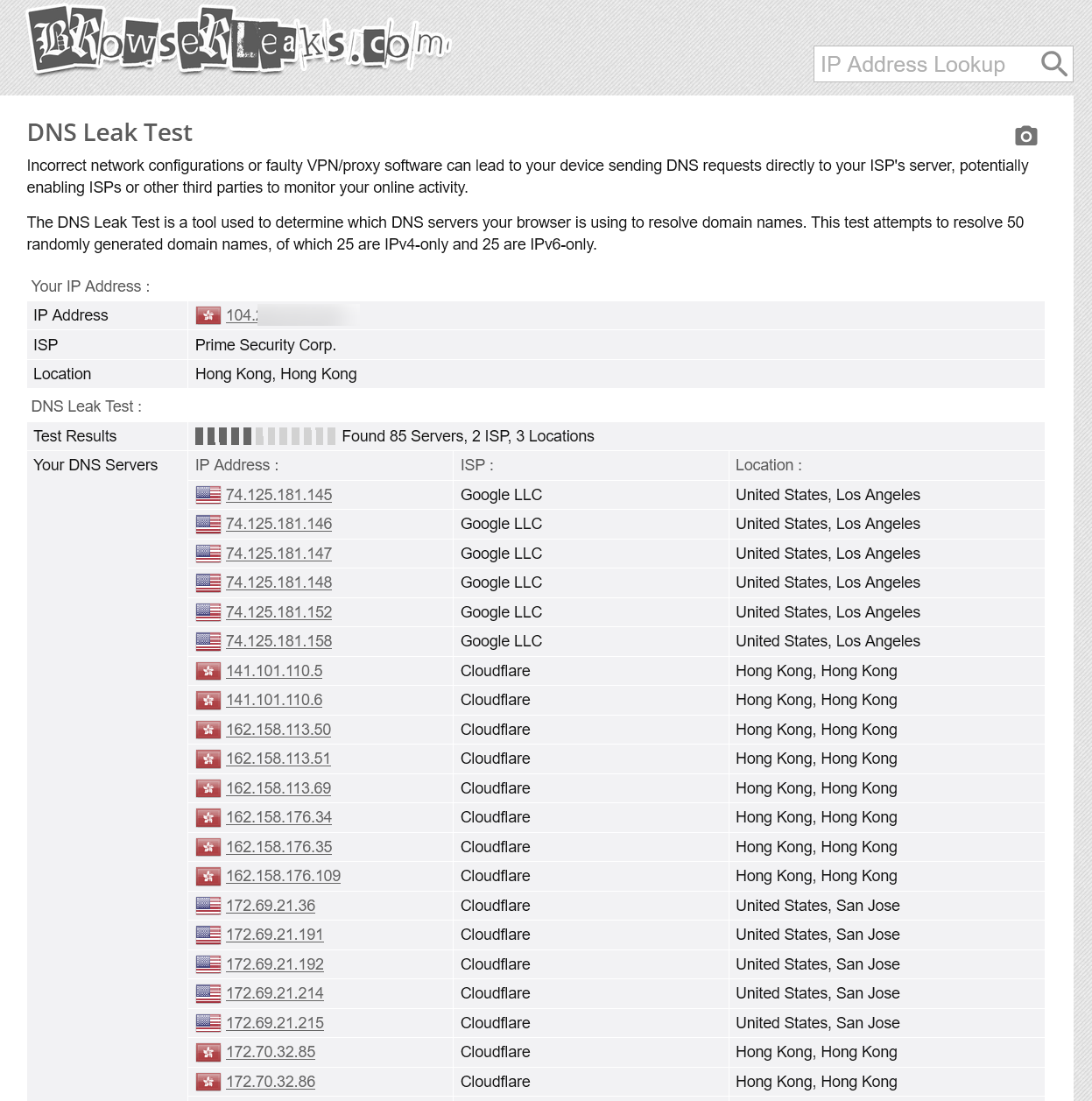
Finally, run a DNS leak test to confirm that the issue has been resolved. If no domestic DNS servers appear, your configuration is correct. Enjoy the network optimisation and leak prevention provided by SmartDNS and Clash!
Reference: https://blog.lololowe.com/posts/8f1e/ ↩︎
SmartDNS is designed to handle latency efficiently. For details, see “How SmartDNS Avoids Slow DNS Resolution Due to Speed Testing”. ↩︎
A collection of Anti AD’s notable missteps is available. ↩︎
